
Resource Guide
The Charter School Cybersecurity Guide: Cybersecurity for Your School
Build a secure digital environment that protects sensitive data and mitigates risks—helping your school stay competitive, relevant, and safe. This resource was created in collaboration with Software MSP, a trusted provider of technology solutions for schools nationwide.
Download Full Guide for FreeWhy Cybersecurity Matters for Your School
Your school handles a vast amount of sensitive data—including student records, financial information, and employee information. Cybersecurity measures help prevent the unauthorized disclosure of personally identifiable information (PII) and maintain compliance with student privacy laws, such as the Family Educational Rights and Privacy Act (FERPA).
Cyberattacks—like ransomware or distributed denial-of-service (DDoS) attacks—can disrupt school operations and negatively impact student learning. Robust cybersecurity measures help safeguard intellectual property from theft, unauthorized access, or infringement. By fostering a culture of cybersecurity, charter schools can empower their students and staff to make informed decisions, protect themselves online, and contribute to a safer digital environment.

Creating Your Incident Response Plan
Even schools with the best safeguards in place can still become victims of a cyberattack. The threat landscape is constantly evolving, and cybercriminals are always looking for new ways to exploit vulnerabilities. It’s essential to have a plan in place if your school becomes a target.
Having a well-defined and practiced Incident Response Plan is essential. The biggest thing to consider is that time is of the essence when a cyberattack occurs. A swift and coordinated response can significantly reduce the attack’s impact and help prevent further consequences, setbacks, and learning loss.
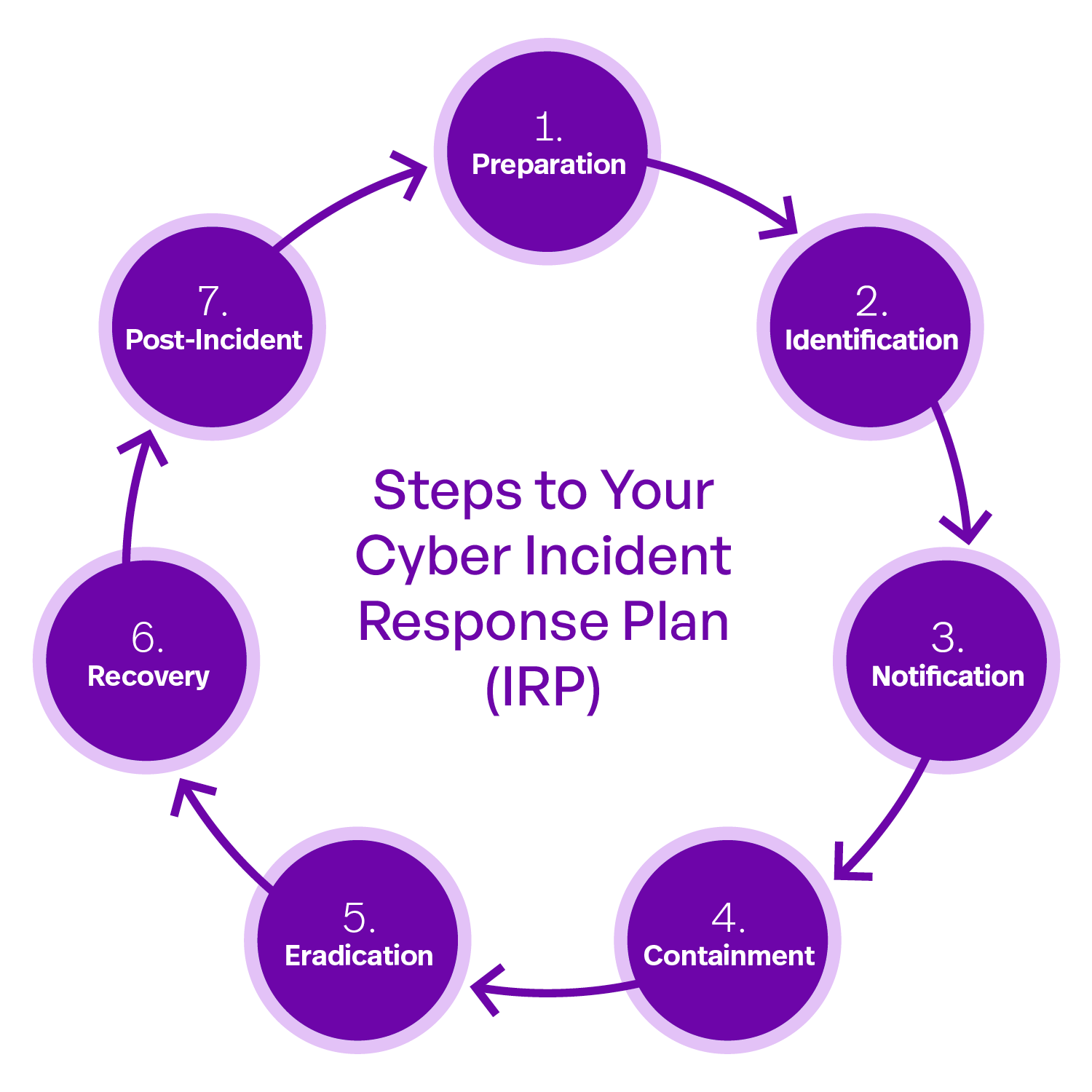
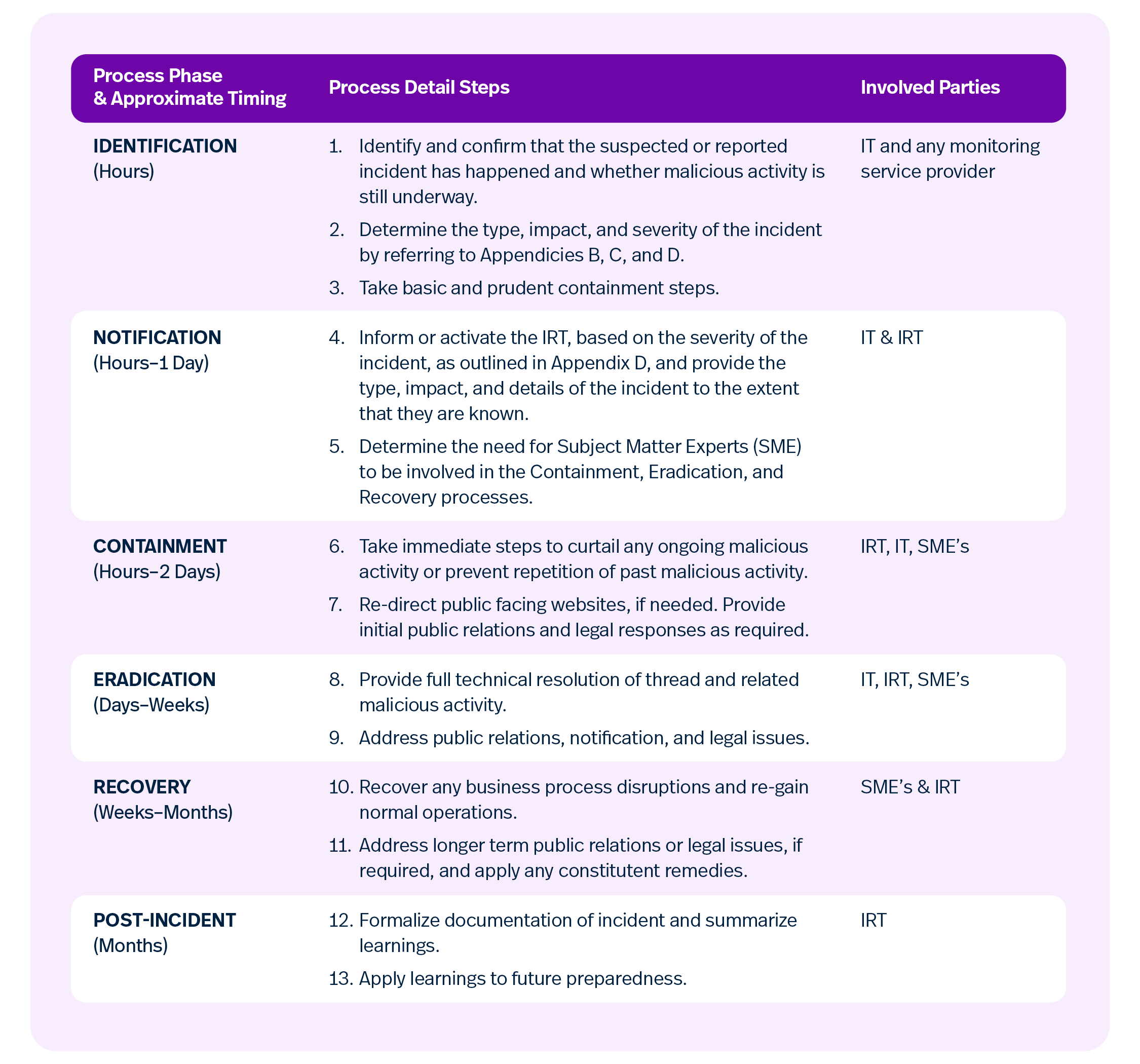
Identify and Train Your Incident Response Team (IRT)
The IRT is a group responsible for coordinating and executing your school’s response when a cyber incident occurs. Their expertise and preparedness are crucial for a well-coordinated response.
Here’s an example timeline to build out with your IRT.
Investing time and effort into information architecture helps create clear, easy, and effective experiences for your users, which ultimately helps your school reach its business goals. Our go-to IA exercises are core modeling and mobile-first prioritization.
Success Story
See Success StoriesSTARS Charter School
STARS partnered for money to run their school. They were able to embark upon building projects with minimal disruptions to their thriving programs. With the new, improved space, STARS has been able to dramatically increase enrollment.
View Case Study
Need money to run your school?
Get Started- Talk to a real person
- Get qualified in minutes
- Fund your school